There is a kind of spambot that I call a Sleeper. It poses as a legitimate account by “stealing” arbitrary tweets from the public timeline and tweeting them as its own. As it follows people, a proportion will follow back. Eventually this account will have built a mature following and can “wake up”. i.e. it can start tweeting its cargo and even send DMs.
These bots are usually easy to spot because their tweets all show as being “From API”, meaning that the update wasn’t sent by a registered app using OAuth. If I was a spammer, I’d be wanting to fix that because it’s a dead give away. I’ve also seen other services such as HelloTxt being used by these bots, but just now I spotted something new. – Tweets from Tweetie.
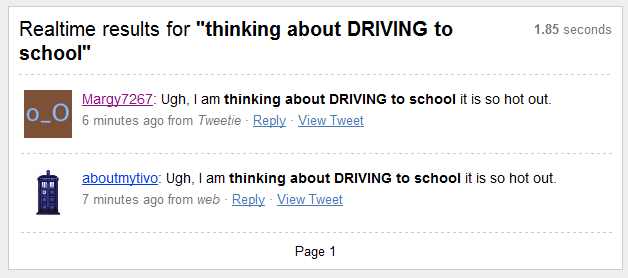
This example (@margy6727) was flagged in a TwitBlock scan due to aggressive following and being largely ignored. This search result shows the original tweet below, and the one above is the bot cloning the tweet and updating somehow via Tweetie.
Now how have they done this?
Have they reverse engineered one of the Tweetie apps and obtained the API key and secret to use in their own bots? Have they developed something that can automate Tweetie externally? (AppleScript was suggested by @pepijndevo). Do they have a sweatshop of chinese teenagers cut-and-pasting for 50 cents/hr? Perhaps there’s some loophole on the Twitter end? Twitter aren’t exactly buttoned up on the security front and they clearly don’t check new app registrations very rigorously.
Suggestions welcome.
[ UPDATE ]
This Twitter FAQ is misleading. I am informed by Tweetie that Basic Auth apps registered “pre-OAuth” can indeed still pass the [now] discontinued source parameter to spoof the user-agent. I just tried it and all you have to do to make your tweet appear to have come from Tweetie is add “source=tweetie” to your API call. That’s a real shame.